Harnessing AWS Signature: A Guide to Secure REST API Authentication
As the landscape of cloud computing evolves, securing access to APIs becomes increasingly crucial. AWS Signature provides a robust mechanism for authenticating requests to AWS services through REST APIs. This article discusses the importance of AWS Signature, explains what it is, provides implementation examples in Java and Go, identifies tools for testing, including EchoAPI, and concludes with the benefits of using AWS Signature.

Why Use AWS Signature for REST APIs
1. Enhanced Security
AWS Signature employs cryptographic techniques to ensure secure authentication. By ensuring that the requests are signed with a secret key, it protects data integrity and authenticity, preventing unauthorized access.
2. Request Integrity
AWS Signature ensures that each request is signed, enabling AWS to verify both the sender's identity and the integrity of the request during transit. This is critical for maintaining the integrity of data.
3. Expiration and Replay Prevention
AWS Signature includes features such as request expiration and nonce values. These features protect against replay attacks by ensuring that each request is unique and only valid for a specified time frame.
4. AWS Compatibility
Since AWS Signature is specifically designed for AWS services, it works seamlessly across different AWS APIs and SDKs, offering a standardized method for authentication.
What is AWS Signature?
AWS Signature is a protocol for creating a secure signed hash of API requests sent to AWS services. It involves several key components:
Access Key ID: A unique identifier associated with an AWS account.
Secret Access Key: A confidential key used to generate a cryptographic hash, ensuring that only authorized users can sign requests.
Canonical Request: A standardized string that includes the HTTP method, request path, query string, and headers.
String to Sign: A string derived from the canonical request, the date, and other elements, which is ultimately signed to create the AWS Signature.
The signed requests are included in the Authorization header, enabling AWS to validate them.
How to Implement AWS Signature in Java
Implementing AWS Signature in Java requires constructing the canonical request and signing it. Here’s a simplified example:
Java Code Example
import java.nio.charset.StandardCharsets;
import javax.crypto.Mac;
import javax.crypto.spec.SecretKeySpec;
import java.security.SignatureException;
public class AWSSignature {
public static void main(String[] args) throws Exception {
String accessKey = "YOUR_ACCESS_KEY";
String secretKey = "YOUR_SECRET_KEY";
String service = "SERVICE_NAME";
String region = "REGION_NAME";
String method = "GET";
String uri = "/your/api/path";
String host = "api.endpoint.com";
// Create the date and time
String date = "DATE"; // Format: YYYYMMDD
String amzDate = "AMZ_DATE"; // Format: YYYYMMDD'T'HHMMSS'Z'
// Create canonical request
String canonicalRequest = createCanonicalRequest(method, uri, host, amzDate);
String stringToSign = createStringToSign(date, region, service, canonicalRequest);
String signature = calculateSignature(secretKey, stringToSign, date, region, service);
// Create the authorization header
String authorizationHeader = "AWS4-HMAC-SHA256 Credential=" + accessKey + "/" + date + "/" + region + "/" + service + "/aws4_request, "
+ "SignedHeaders=host;x-amz-date, Signature=" + signature;
// Use the authorization header in your HTTP request
System.out.println("Authorization Header: " + authorizationHeader);
}
// Placeholder for createCanonicalRequest, createStringToSign, and calculateSignature methods
}
Ensure you implement 'createCanonicalRequest', 'createStringToSign', and 'calculateSignature' methods to complete the process.
How to Implement AWS Signature in Go
In Go, you can use the crypto/hmac and crypto/sha256 packages to generate the AWS Signature. Here’s a basic example:
Go Code Example
package main
import (
"crypto/hmac"
"crypto/sha256"
"encoding/hex"
"fmt"
"time"
)
func calculateSignature(secretKey, stringToSign string) string {
mac := hmac.New(sha256.New, []byte(secretKey))
mac.Write([]byte(stringToSign))
return hex.EncodeToString(mac.Sum(nil))
}
func main() {
accessKey := "YOUR_ACCESS_KEY"
secretKey := "YOUR_SECRET_KEY"
method := "GET"
uri := "/your/api/path"
host := "api.endpoint.com"
region := "REGION_NAME"
service := "SERVICE_NAME"
date := time.Now().UTC().Format("20060102")
amzDate := time.Now().UTC().Format("20060102T150405Z")
canonicalRequest := createCanonicalRequest(method, uri, host, amzDate)
stringToSign := createStringToSign(date, region, service, canonicalRequest)
signature := calculateSignature(secretKey, stringToSign)
authorizationHeader := fmt.Sprintf("AWS4-HMAC-SHA256 Credential=%s/%s/%s/%s/aws4_request, SignedHeaders=host;x-amz-date, Signature=%s",
accessKey, date, region, service, signature)
// Use the authorization header in your HTTP request
fmt.Println("Authorization Header:", authorizationHeader)
}
// Placeholder for createCanonicalRequest and createStringToSign methods
Make sure to implement the 'createCanonicalRequest' and 'createStringToSign' methods to complete the implementation.
How to Use Tools to Test AWS Signature
Testing AWS Signature can be performed through various tools:
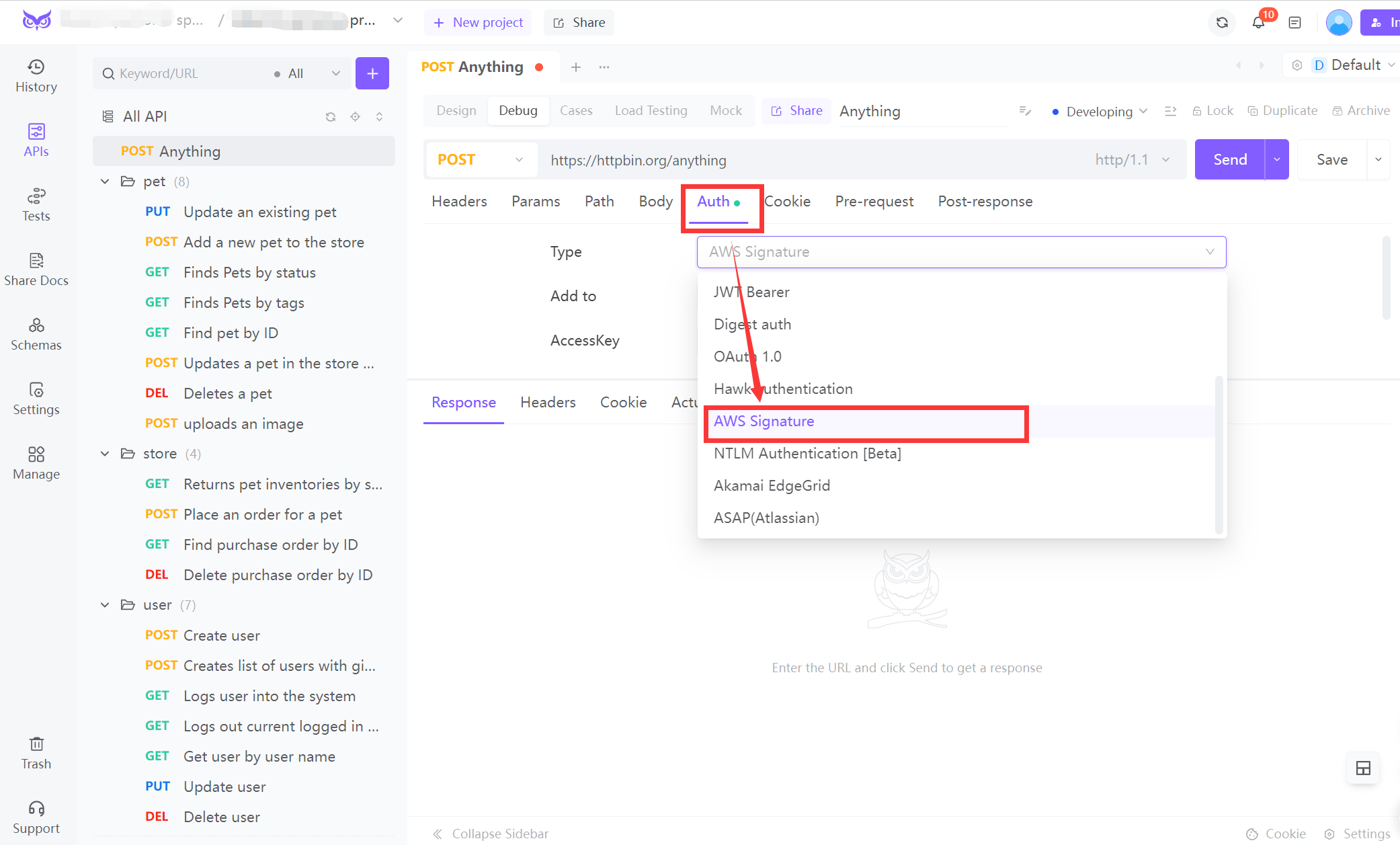
1. EchoAPI
EchoAPI is a user-friendly tool for creating and sending HTTP requests with the required headers. It simplifies testing by providing an interface where you can input your request details and view the responses. Simply paste your Authorization header and examine how your API responds to signed requests.
2. Postman
Postman allows you to create HTTP requests with custom headers. You can manually set the Authorization header with the generated AWS Signature and examine the responses from your API.
3. cURL
Using cURL, you can make command-line requests to test your API endpoints, including all necessary headers, including the AWS Signature.
4. Automated Testing
Automated testing libraries can be used in both Java (JUnit) and Go (testing package) to script tests that verify AWS Signature generation and functionality.
Conclusion
AWS Signature is a crucial protocol for securing REST APIs interacting with AWS services. It provides strong security features, including message integrity and replay prevention. Implementing AWS Signature in programming languages like Java and Go involves creating a canonical request and generating a secure hash. Testing tools like EchoAPI, Postman, and cURL facilitate the validation of your implementation, ensuring your API remains secure. Embracing AWS Signature enhances user trust and protects sensitive data, making it a valuable choice for API development.
Try EchoAPI Interceptor today!